
More privacy control for all with the TinyCheck tool
To increase privacy control over users’ data, two Kaspersky experts have combined the results of their research and upgraded the openly available TinyCheck tool. Initially developed as a stalkerware detection tool for service organizations working with victims of domestic violence, TinyCheck now also offers help to uncover all types of geo-tracking apps.
In December 2020, Apple and Google prohibited any apps in their stores that use X-Mode’s technology that secretly enables tracking and selling of location data. Several months prior to the tech companies’ decision, Kaspersky’s Global Research and Analysis Team (GReAT) director, Costin Raiu started to analyze such apps after he had seen a visualization that identified people’s movements using their GPS data made available by X-Mode.
Raiu found more than 240 distinct apps with X-Mode’s tracking technology which in total have been installed more than 500 million times. Such data collection becomes possible when developers embed a component – a software development kit (SDK) – in their app. The problem with these tracking SDKs is that it is impossible for a user to tell whether an app contains such location tracking components. Also, the app may have a legitimate reason to ask for the user’s location as many rely on location to function properly, but such an app might also sell the GPS data.
In addition, any app can contain more than just one tracking SDK. For example, while Raiu was looking at an app that included the X-Mode SDK in question, he discovered five other components from other companies that were also collecting location data.
Making life harder for secret trackers
Now, Raiu’s findings have been integrated into TinyCheck, an open-source tool developed and published in November last year by Félix Aimé, another of Kaspersky’s GReAT experts. Initially, TinyCheck was designed to help tackle the issue of stalkerware.
Stalkerware is software used to secretly spy on another person’s private life via a smart device and also installed without the user’s knowledge. While often used to facilitate violence against an intimate partner, the software may also be used in a different context. TinyCheck can now detect both stalkerware and tracking apps, but the tool issues two different alerts to the user.
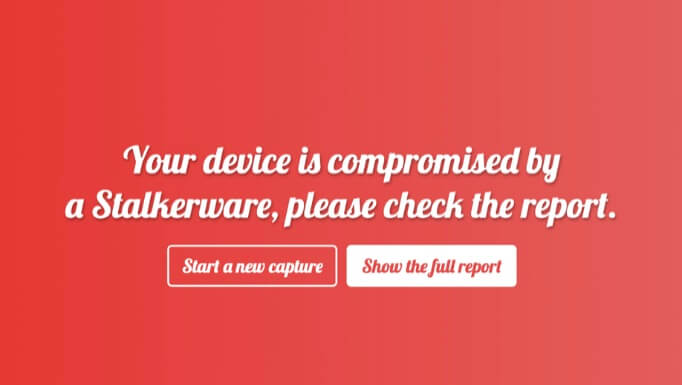
Figure 1 A TinyCheck alert when stalkerware is detected.

Figure 2 A TinyCheck alert when geo-tracking apps are detected.
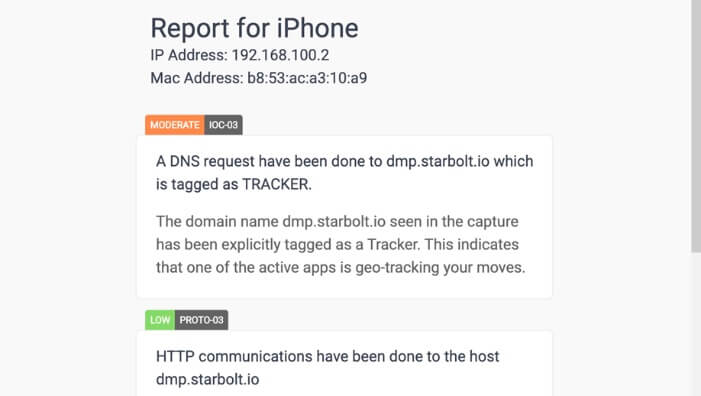
Figure 3 an excerpt of the TinyCheck report on any detected geo-tracking apps.
Using a regular Wi-Fi connection, TinyCheck scans a mobile device’s outgoing traffic and identifies interactions with known malicious sources. In order to make use of TinyCheck, a computer with a Raspberry Pi OS Buster is needed along with one of the following two options: either two Wi-Fi interfaces, one for connecting to the internet and one for your mobile’s connectivity (AP mode), or one Wi-Fi interface and an Ethernet connection for internet. In both cases, the best choice is a Raspberry Pi Model 3 or higher with a small touch screen.

Figure 4 A visualization of how TinyCheck works.
“Secret tracking of users and using their data without their knowledge should not happen for any reason. Having the combined list of indicators of compromise for mobile trackers and stalkerware integrated in TinyCheck, users are able to increase their privacy control. TinyCheck is therefore designed as an open source tool that is freely available to anyone, and one which the security community can share and contribute their knowledge to,” comments Félix Aimé, a Kaspersky GReAT security researcher.
In addition to using TinyCheck, there are a few tips to follow to lower the chances of being tracked by such apps and services, which involve limiting apps’ permissions:
- Check which apps have permission to use your location? The following information shows how to perform such checks on an Android 8 device (later versions do not differ significantly) and an iOS device. If an app does not need location permission, you can simply revoke it.
- Give apps permission to use your location only while they are being used. Most apps do not need to know your location when they are running in the background, making this setting ideal for many of them.
- Delete apps that are not used anymore. If the app has not been opened in a month or more, it is probably safe to assume it is no longer needed; and if this changes in the future, it can always be reinstalled.
- Use proven cybersecurity protection, such as Kaspersky Internet Security for Android, which protects you against all kinds of mobile threats.
To read about the TinyCheck installation process, please visit https://github.com/KasperskyLab/tinycheck#readme











































